
When Apple released the latest version 11.3 for macOS on Monday, it didn't just introduce support for new features and optimizations. More importantly, the company fixed a zero-day vulnerability that hackers were actively exploiting to install malware without triggering core Mac security mechanisms, some that were in place for more than a decade.
Together, the defenses provide a comprehensive set of protections designed to prevent users from inadvertently installing malware on their Macs. While one-click and even zero-click exploits rightfully get lots of attention, it’s far more common to see trojanized apps that disguise malware as a game, update, or other desirable piece of software.Protecting users from themselves
Apple engineers know that trojans represent a bigger threat to most Mac users than more sophisticated exploits that surreptitiously install malware with minimal or no interaction from users. So a core part of Mac security rests on three related mechanisms:
- File Quarantine requires explicit user confirmation before a file downloaded from the Internet can execute.
- Gatekeeper blocks the installation of apps unless they’re signed by a developer known to Apple.
- Mandatory App Notarization permits apps to be installed only after Apple has scanned them for malware.
Earlier this year, a piece of malware well known to Mac security experts began exploiting a vulnerability that allowed it to completely suppress all three mechanisms. Called Shlayer, it has an impressive record in the three years since it appeared.
Last September, for instance, it managed to pass the security scan that Apple requires for apps to be notarized. Two years ago, it was delivered in a sophisticated campaign that used novel steganography to evade malware detection. And last year, Kaspersky said Shlayer was the most detected Mac malware by the company’s products, with almost 32,000 different variants identified.Clever evasion
Shlayer’s exploitation of the zero-day, which started no later than January, represented yet another impressive feat. Rather than using the standard Mach-O format for a Mac executable, the executable component in this attack was the macOS script, which executes a series of line commands in a particular order.
Normally, scripts downloaded from the Internet are classified as application bundles and are subject to the same requirements as other types of executables. A simple hack, however, allowed scripts to completely shirk those requirements.
By removing the info.plist—a structured text file that maps the location of files it depends on—the script no longer registered as an executable bundle to macOS. Instead, the file was treated as a PDF or other type of non-executable file that wasn’t subject to Gatekeeper and the other mechanisms.
One of the attacks began with the display of an ad for a fake Adobe Flash update:
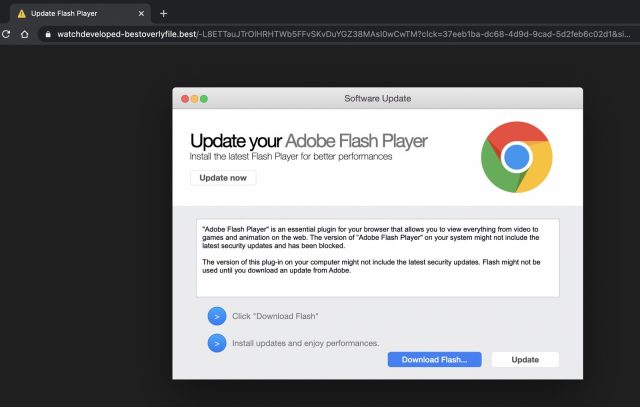
The videos below show what a big difference the exploit made once someone took the bait and clicked download. The video immediately below depicts what the viewer saw with the restrictions removed. The one below that shows how much more suspicious the update would have looked had the restrictions been in place.
The bug, which is tracked as CVE-2021-30657, was discovered and reported to Apple by security researcher Cedric Owens. He said he stumbled upon it as he was using a developer tool called Appify while performing research for a “red team” exercise, in which hackers simulate a real attack in an attempt to find previously overlooked security weaknesses.
“I found that Appify was able to turn a shell script into a double clickable ‘app’ (really just a shell script inside of the macOS app directory structure but macOS treated it as an app),” he wrote in a direct message. “And when executed it bypasses Gatekeeper. I actually reported it pretty quickly after discovering it and did not use it in a live red team exercise.”
Apple fixed the vulnerability with Monday’s release of macOS 11.3. Owens said that the flaw appears to have existed since the introduction of macOS 10.15 in June 2019, which is when notarization was introduced.
Owens discussed the bug with Patrick Wardle, a Mac security expert who previously worked at Jamf, a Mac enterprise security provider. Wardle then reached out to Jamf researchers, who uncovered the Shlayer variant that was exploiting the vulnerability before it was known to Apple or most of the security world.
“One of our detections alerted us to this new variant, and upon closer inspection we discovered its use of this bypass to allow it to be installed without an end user prompt,” Jamf researcher Jaron Bradley told me. “Further analysis leads us to believe that the developers of the malware discovered the zeroday and adjusted their malware to use it, in early 2021.”
Wardle developed a proof-of-concept exploit that showed how the Shlayer variant worked. After being downloaded from the Internet, the executable script appears as a PDF file named Patrick’s Resume. Once someone doubleclicks on the file, it launches a file called calculator.app. The exploit could just as easily execute a malicious file.

In a 12,000-word deep-dive that delves into the causes and effects of the exploits, Wardle concluded:
Though this bug is now patched, it clearly (yet again) illustrates that macOS is not impervious to incredible shallow, yet hugely impactful flaws. How shallow? Well that fact that a legitimate developer tool (appify) would inadvertently trigger the bug is beyond laughable (and sad).
And how impactful? Basically macOS security (in the context of evaluating user launched applications, which recall, accounts for the vast majority of macOS infections) was made wholly moot.
Bradley published a post that recounted how the exploit looked and worked.
Many people consider malware like Shlayer unsophisticated because it relies on tricking its victims. To give Shlayer its due, the malware is highly effective, in large part because of its ability to suppress macOS defenses designed to tip-off users before they accidentally infect themselves. Those who want to know if they've been targeted by this exploit can download this python script written by Wardle.
Article From & Read More ( Actively exploited Mac 0-day neutered core OS security defenses - Ars Technica )https://ift.tt/3nqNI3V
Bagikan Berita Ini














0 Response to "Actively exploited Mac 0-day neutered core OS security defenses - Ars Technica"
Post a Comment